-
Notifications
You must be signed in to change notification settings - Fork 1.3k
(ccc2021 hackathon ) kvm: add hosts using cloudstack ssh private key #5684
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
(ccc2021 hackathon ) kvm: add hosts using cloudstack ssh private key #5684
Conversation
|
@blueorangutan package |
|
@weizhouapache a Jenkins job has been kicked to build packages. I'll keep you posted as I make progress. |
| final String privateKey = _configDao.getValue("ssh.privatekey"); | ||
| if (!SSHCmdHelper.acquireAuthorizedConnectionWithPublicKey(sshConnection, username, privateKey)) { | ||
| s_logger.error("Failed to authenticate with ssh key"); | ||
| if (!sshConnection.authenticateWithPassword(username, password)) { |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Nit - maybe do a check if password was even passed (empty?)
|
Left some comments but nice hack @weizhouapache ! |
|
(of course your changes are closer to what maybe reviewed/tested merged so I'm being very thorough otherwise LGTM!) |
 yadvr
left a comment
yadvr
left a comment
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
LGTM
ui/src/views/infra/HostAdd.vue
Outdated
| <div class="form__label"><span class="required">* </span>{{ $t('label.password') }}</div> | ||
| <span class="required required-label">{{ $t('label.required') }}</span> | ||
| <div class="form__item" v-if="selectedClusterHyperVisorType !== 'VMware'"> | ||
| <div class="form__label">{{ $t('label.password') }}</div> |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Maybe be have it not required just for kvm? (for ex. required for xenserver?)
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
ping @weizhouapache when you've time - why not put explicit checks for example a radio/button or toggle to switch between password or ssh-key auth just for KVM (however for XenServer too this feature can be done).
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
@rhtyd
good idea. will make the UI change.
let's support kvm at first, then xenserver (this is not needed for vmware).
| if (StringUtils.isNotBlank(privateKey)) { | ||
| File privateKeyFile = null; | ||
| try { | ||
| privateKeyFile = File.createTempFile("cloudstack-host-", null); |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
@weizhouapache
This temp. hack may not be required as mgmt server saves the ssh private/pub keys at: /var/lib/cloudstack/management/.ssh/id_rsa on the mgmt server, why not just read/use that?
In fact if this is saved/assumed, then we don't even need to read the private key from db and pass it here. Thoughts?
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Note: needs checking on all distros (this path), on centos7, centos/rocky8, ubuntu and suse. cc @davidjumani if you know/remember distro specific paths.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
@weizhouapache This temp. hack may not be required as mgmt server saves the ssh private/pub keys at:
/var/lib/cloudstack/management/.ssh/id_rsaon the mgmt server, why not just read/use that?In fact if this is saved/assumed, then we don't even need to read the private key from db and pass it here. Thoughts?
@rhtyd
I have considered it. but at the end I decided to use temp file so that the process will not rely on any file on management server.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
In that case let's fix the mod bits of the file to be just read-only (0400)
|
Packaging result: ✔️ el7 ✔️ el8 ✔️ debian ✔️ suse15. SL-JID 1699 |
 DaanHoogland
left a comment
DaanHoogland
left a comment
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
looks good, just one attack vector (of questionable vulnerability admitted). We might need to revisit that part. Also documentation on how to use it/prepare hosts will be needed.
Good Job @weizhouapache
| return false; | ||
| } | ||
| try { | ||
| if (!sshConnection.authenticateWithPublicKey(username, privateKeyFile, null)) { |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
@weizhouapache can we pass the privatekey content to this method (or similar available methods)?
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
@rhtyd yes, I will use char[], testing it.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
@rhtyd @DaanHoogland
updated this PR to use char[] in server authentication. thanks for your review !
|
@blueorangutan package |
|
@blueorangutan test keepEnv |
|
@weizhouapache a Trillian-Jenkins test job (centos7 mgmt + kvm-centos7) has been kicked to run smoke tests |
|
@weizhouapache this is not in draft, is it ready for merge? (just making sure) |
@DaanHoogland |
|
@DaanHoogland @rhtyd |
382d6a8 to
045fa5a
Compare
| s_logger.debug("Failed to authenticate"); | ||
| throw new DiscoveredWithErrorException("Authentication error"); | ||
|
|
||
| final String privateKey = _configDao.getValue("ssh.privatekey"); |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
@weizhouapache I think, it is better to try with ssh key or password (based on the authentication mode), not with other when one of it fails. You can determine authentication mode, either from the user input or may be from password/privatekey config.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
@sureshanaparti
isn't it better to support both ? hosts are still manageable if one of the authentication fails.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
if one authentication fails, try other may not be good.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
if one authentication fails, try other may not be good.
@sureshanaparti ok. let's ask other guys.
@rhtyd @DaanHoogland what's your opinion ?
|
@weizhouapache Does multiple kvm hosts in a cluster supports different authentication mechanism (few with passwords, and others with ssh key)? If so, is this info maintained in management server? |
|
LGTM, @weizhouapache is this ready for testing ? cc @borisstoyanov @vladimirpetrov |
|
@rhtyd a Jenkins job has been kicked to build packages. I'll keep you posted as I make progress. |
@rhtyd yes, it is ready for review and testing. |
|
@weizhouapache a Jenkins job has been kicked to build packages. I'll keep you posted as I make progress. |
@sureshanaparti yes, if I think the main issue for now is, password authentication does not work sometimes, for example by ssh protocol, incorrect ssh settings, wrong password, password is changed. it should not be a problem/risk to ssh from mgmt server to hosts by both options, as they all use internal IPs. |
|
Packaging result: ✔️ el7 ✔️ el8 ✔️ debian ✔️ suse15. SL-JID 1828 |
|
@blueorangutan test |
|
@weizhouapache a Trillian-Jenkins test job (centos7 mgmt + kvm-centos7) has been kicked to run smoke tests |
|
Trillian Build Failed (tid-2615) |
|
Packaging result: ✔️ el7 ✔️ el8 ✔️ debian ✔️ suse15. SL-JID 1829 |
|
@blueorangutan test |
1 similar comment
|
@blueorangutan test |
|
@sureshanaparti a Trillian-Jenkins test job (centos7 mgmt + kvm-centos7) has been kicked to run smoke tests |
|
Trillian test result (tid-2616)
|
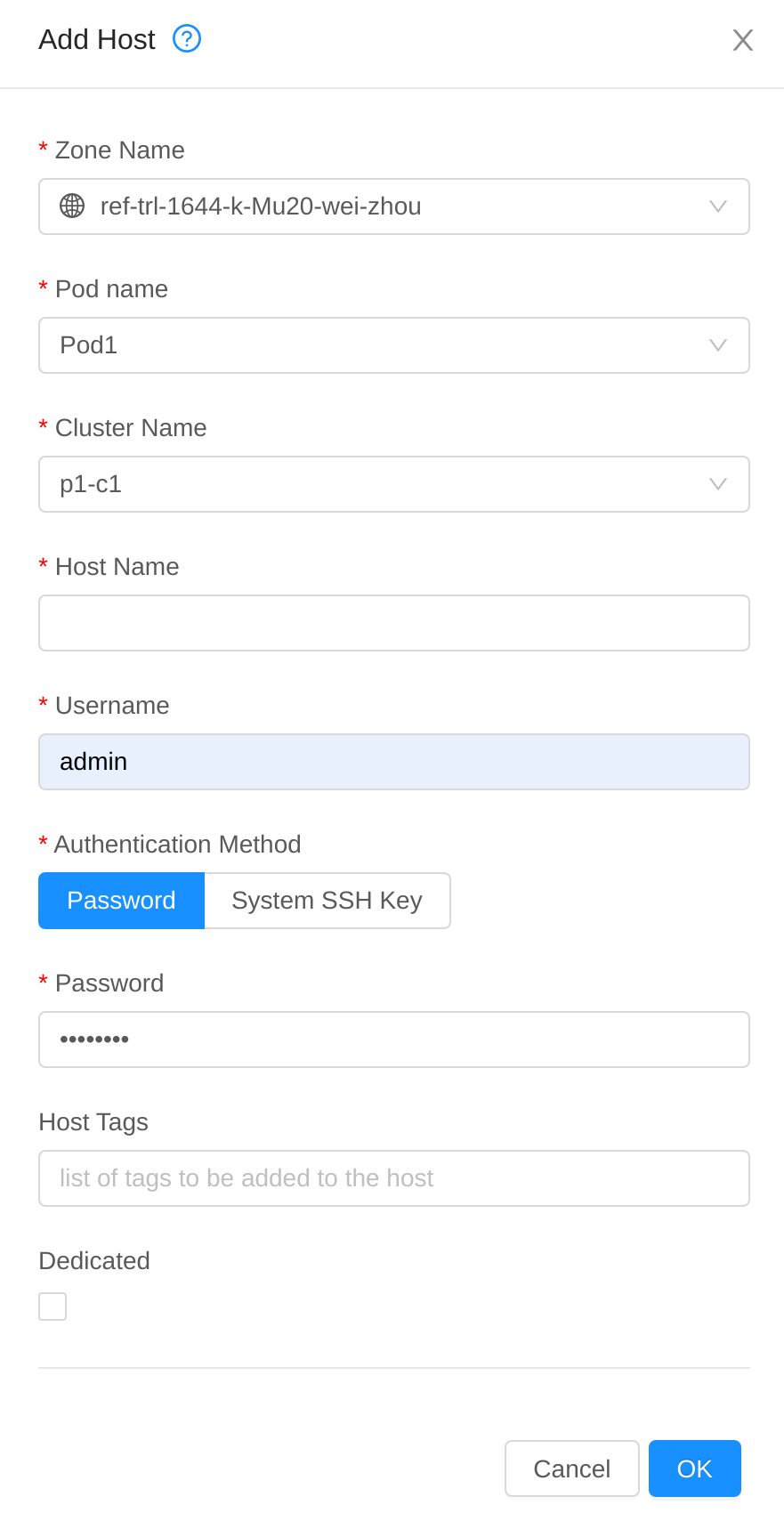
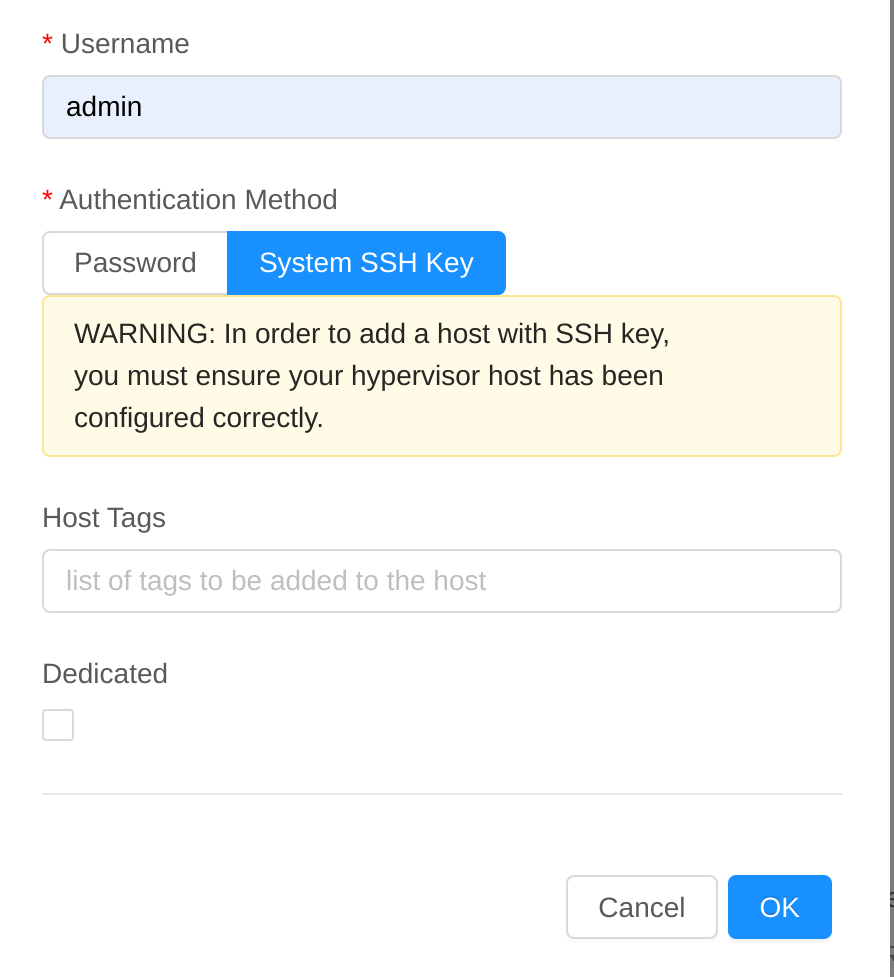
Description
This PR provides the option to add kvm hosts with empty or wrong password.
To support this, the cloudstack ssh public key needs to be added in the ~/.ssh/authorized_keys on host.
Thanks @rhtyd for the idea !
Types of changes
Feature/Enhancement Scale or Bug Severity
Feature/Enhancement Scale
Screenshots (if appropriate):
How Has This Been Tested?
add host, with correct password, works as expected.
put host to maitenance, stop cloudstack-agent, cancel maintenance, remove the host. all work.
add host, with empty password (ssh public key is added to ~/.ssh/authorized_keys), works as expected.
put host to maitenance, stop cloudstack-agent, cancel maintenance. all work as expected.